POSITIONING technologies are already part and parcel of daily life and business across Australia – from using Google Maps on smartphones to emergency management and farming – but there is a lot more to come.
With increasing us and new technologies to come, the Australian Government has announced an investment of $12 million in a two-year program looking into the future of positioning technology in Australia.
Federal Minister for Infrastructure and Transport Darren Chester said the funding would be used to test “instant, accurate and reliable positioning technology that could provide future safety, productivity, efficiency and environmental benefits across many industries in Australia” including transport, agriculture, construction, and resources. 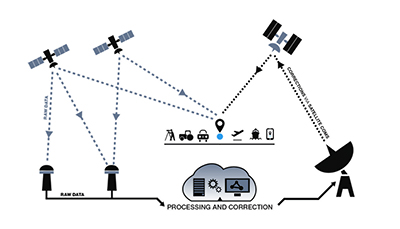
Research used by the government indicated the wide-spread adoption of improved positioning technology had the potential to generate upwards of $73 billion of value to Australia by 2030.
Mr Chester said the program could test the potential of Satellite Based Augmentation System (SBAS) technology in the four transport sectors—aviation, maritime, rail and road.
“SBAS utilises space-based and ground-based infrastructure to improve and augment the accuracy, integrity and availability of basic Global Navigation Satellite System (GNSS) signals, such as those currently provided by the USA Global Positioning System (GPS),” Mr Chester said.
The future use of SBAS technology was strongly supported by the aviation industry to assist in high accuracy GPS-dependent aircraft navigation.
“Positioning data can also be used in a range of other transport applications including maritime navigation, automated train management systems and in the future, driverless and connected cars,” Mr Chester said.
Minister for Resources and Northern Australia, Matt Canavan said access to more accurate data about the Australian landscape would also help unlock the potential of the North.
“This technology has potential uses in a range of sectors, including agriculture and mining, which have always played an important role in our economy, and will also be at the heart of future growth in Northern Australia,” Senator Canavan said.
“Access to this type of technology can help industry and government make informed decisions about future investments.”
The two-year project will test SBAS technology that has the potential to improve positioning accuracy in Australia to less than five centimetres. Currently, positioning in Australia is usually accurate to 5-10m.
Mr Chester said the SBAS test-bed is Australia's first step towards joining countries such as the US, Russia, India, Japan and many across Europe in investing in SBAS technology and capitalising on the link between precise positioning, productivity and innovation.
The Minister said Geoscience Australia, with the Collaborative Research Centre for Spatial Information (CRCSI), would soon call for organisations from a number of industries including agriculture, aviation, construction, mining, maritime, rail, road, spatial, and utilities to participate in the test-bed.
www.ga.gov.au
ends



